5 strategies to improve your incident communication

TL;DR:
- Clear and regular communication is crucial for effective incident response.
- Investing time in improving incident communication can lead to faster issue resolution and increased customer trust.
- Tailoring communication to different groups reduces stress and maintains goodwill.
- Having a well-defined incident communication plan, assigning clear roles, and utilizing templates are key steps to improving incident communication.
- Regularly revisiting and refining the incident communication process is essential for continuous improvement.
No matter the size or stage of your business, communication is critical. This increases tenfold once you start bringing incidents into the equation.
If you aren’t prioritizing clear and regular communication during incidents, it’s fair to say that your response process is falling short of its potential.
As a team, we’ve written pretty extensively about the importance of communication. And we've designed many incident.io features to help improve businesses' collaboration and communication, both internally and externally.
Just take our recent Status Pages launch as an example, which was designed to address some of the pain points around sharing external communication during incidents. But additional features such as Follow-Ups and Workflows ensure that all loose ends are tied up internally, and the right folks are “in-the-room” during incidents.
In short, we've aimed to give folks all the right tools to manage both internal and external communication during incidents effectively.
For our team, communication is a founding principle. But having a plan around incident communication has been a big part of this.
An incident communication plan is vital to your response since it guides your teams as they give information to stakeholders and customers. It provides them guardrails and ensures that every bit of shared data is as helpful as possible to keep folks on the same page.
Here, you’ll find a list of valuable strategies for improving your incident response readiness through effective communication, many of which our engineers use themselves!
What is incident communication?
Incident communication is the process of effectively and efficiently communicating information about an incident to relevant stakeholders in an incident channel, externally to customers, or some other medium.
Hint: this is the type of incident workflow that status pages, both internal and external, are perfect for.
Good incident communication plays a crucial role in managing and mitigating the impact of incidents, such as extended downtime, which inevitably frustrates customers.
One of the major benefits of good incident communication is that information is shared on time, which helps keep other responders and affected parties in the loop. This eliminates the need for context-chasing during an incident, which can go a long way toward resolving issues faster.
Why investing time to improve incident communication is worth the effort
It’s worth stressing that there’s a lot to lose from lackluster incident communication.
When responders are parsing unclear comms or don’t have the critical context they need to figure out what’s happening, downtime grows much more. And when downtime gets extended by even a fraction, customers lose patience, and ultimately, trust.
Whether you’re focusing on internal or external comms, by investing time in improving them, issues tend to get resolved faster since there’s less ambiguity, and customers gain more trust in your ability to keep them in the loop, even when things are going haywire.
But remember today, an incident can create issues on any front. In other words, incidents aren’t siloed to engineering teams—they can touch everything from customer success to legal.
Because of this, modern incident response requires cross-disciplined team involvement and solid comms to match.
Improving your incident communication in five steps
To start, improving your communication plan requires rethinking how incidents affect users.
A poorly performing app or a major incident like a security breach isn’t isolated to a single user group—it affects several. Because of this, you can’t take a blanket approach to communication.
Tailoring communication to apply to affected groups reduces stress, but it also keeps goodwill levels high.
The nature of each situation and who the incident impacts will drive your communications. For example, you wouldn’t communicate with marketing folks like you would engineers. Why? Because each of these groups has different levels of understanding in certain areas.
Ramp, as an example, is a corporate credit card company with a user base primarily of consumers making everyday business purchases. So if they have an incident, it’s unlikely that they’ll dive into a screed of technical speak to explain what’s going on. But if that same incident happened at Jira, then going into technical detail would likely be appropriate.
But whichever industry you’re in, you should aim to resolve the incident without breaking customer trust or decreasing your team’s confidence. You also want to take away valuable learnings from the incident, which will give you important insights to improve your response over time.
Here are five steps that you can follow to improve your incident communication and build a more resilient response process and improve customer trust.
Step # 1: Have an incident communication plan ready
Preparation and planning are everything, so it’s critical to implement your plan before an incident occurs.
Responders need time to review their communication roles to understand the timing and purpose of sharing information, no matter the situation.
Your plan should define the go-to process for alerting and involving relevant teams. The stage and scope of the incident can and should help you decide which individuals to bring in and in what order.
The same holds for external communication. Your plan should outline how and when to update customers or affected users through a status page, for example. Your communication plan should also include using public channels to monitor customer reactions. Here at incident.io, we have individual Slack channels where we take note of any chatter happening that would be cause for concern.
Coordinating these different types of incident communication efforts is vital to the success of your response. Your team should be comfortable sharing internal or external updates with appropriate timeliness. But to do this confidently, they should know that the communication plan is reliable and trust that it will guide them through the process accordingly.
It is best to rehearse your incident communication plan throughout your organization. This way, your teams’ communications will exude confidence when an incident occurs.
💭 Pro tip: our engineering team has hosted Game Days in the past as a way to stress test their incident response processes and identify any areas for improvement.
Step # 2: Assign your incident team clearly defined roles and responsibilities
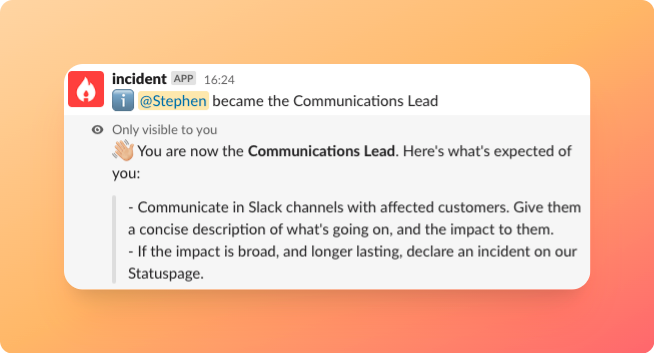
Each team contributes to incident response communication activities in its own way. Typically, plans define roles, and multiple team members receive training to handle those roles.
All departments assume an incident response communication role. The technical teams focus on onboarding individuals with the right skills to solve the immediate problem. Their communications center around internal channels.
However, one tech role informs the non-technical teams on the response status. They, in turn, make an announcement and connect with customers, users, and executive groups affected by the incident.
An appropriately timed flow of authoritative information tamps down misleading rumors about the incident. In addition, the response runs more smoothly when each stakeholder group knows where it stands throughout the resolution process.
Step # 3: Utilize incident communication templates
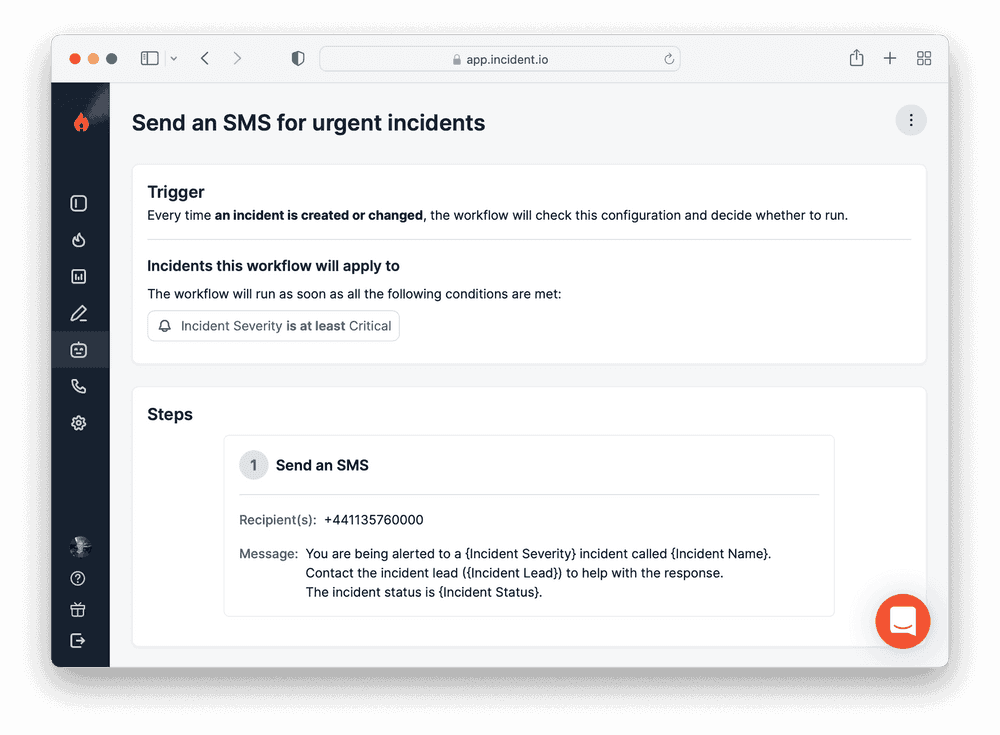
Sharing the correct information builds confidence in your team’s abilities. Using incident communication templates helps achieve this by standardizing inputs.
Rules-based entry keeps data consistent. Templates ensure team members share information at each stage of the process. And templates use mandatory fields to build complete and correct messages.
Accurate documentation is another benefit templates provide. They supply a record of each communication. Collecting and analyzing data at the end of an incident helps you quickly recognize trends and resolve future issues.
Step # 4: Provide regular updates
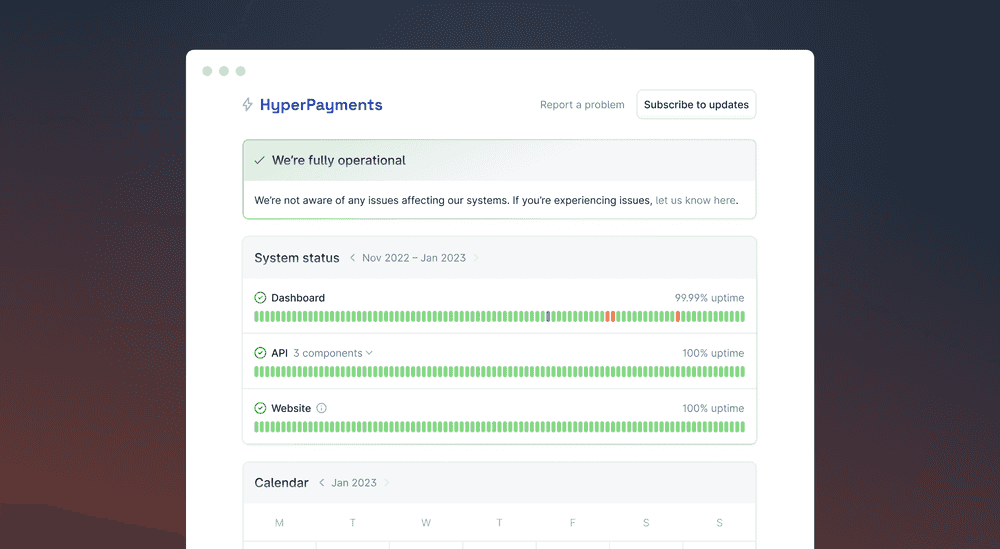
A sound communication strategy includes regular status updates for each stakeholder group. Since incidents affect groups differently, you should provide each with appropriate context and depth.
Communication with internal teams includes the steps taken by other team members. They also learn what they must do to help resolve the incident. First, on dedicated channels, section team leaders discuss the incident. Then, they decide when to notify other groups or individuals to join or drop out of the response.
External parties care about how long a resolution will take. They need outage estimates to plan workarounds for essential tasks. They also want assurances of their data’s integrity. In the end, the incident is delaying their daily work.
Customers tend to assume the worst. Keep them informed to ease their feelings of disappointment. If they know your focus is on solving the immediate problem and preventing it from re-occurring, they will likely forgive some inconvenience.
Providing everyone with regular updates helps keep them on your side.
Step # 5: Periodically revisit and refine your incident communication process
Your incident communication plan is always in development. Each incident provides you with more ways to improve messaging.
Developers regularly update incident monitoring tools. Therefore, you should integrate the latest methods into your incident communication plan. In addition, keeping up to date will help you increase your ability to share information during incidents.
Growing cloud interconnectivity also increases the need for regular incident communication plan updates, as does the evolving cyber threat landscape, where frequent security incidents trigger incident responses.
Add enhancements to your communication plan after going through each incident. The data you get lets you analyze the effects of your response team’s actions and adjust your plan accordingly.
Why does practical communication matter in incident management?
During an incident, everyone focuses on resolving the issue.
But response teams shouldn’t treat communication with affected users as an afterthought. Unfortunately, this common misstep can contribute to the alienation of your customers and stakeholders. And once users feel cut out of the loop, winning back their trust is hard.
When companies need to do more toward developing their incident communication plans, it shows. Each incident becomes more of a struggle than a learning experience.
In this environment, team members often feel insecure about their abilities to manage incident communication challenges. In addition, they’ve often spent much of their emotional capital and find the stress associated with incidents hard to bear.
Incomplete or inconsistent records often lead response teams to repeat mistakes and miss opportunities across multiple incidents. So, to see positive results, response teams should be intentional about investing the necessary resources in documentation, iteration and analysis of incident communication.
Strategic communication planning creates an environment of constant improvement. The communication plan explains the protocol in detail. The best ones leave nothing to chance, keeping every affected party in the communication loop at the correct times.
The results are customers, users, and internal teams all agreeing that your incident communication exceeds expectations. By not leaving anyone in the dark, you build the trust your organization needs on all sides to continue to thrive and grow.

See related articles

4 roles to have on your incident response team for efficiency and the fastest resolution times
Incident response teams work best when they're structured appropriately and have dedicated roles. Here are some best practices for doing just that.
 incident.io
incident.io
Nine incident management solutions to improve your response workflows
Looking for ways to streamline your incident workflow? Here's a list of 9 key incident management solutions and integrations.
 Luis Gonzalez
Luis GonzalezSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



