Free calculators, new ways to escalate, and mushroom farmers

👋 Hey folks
Greetings! It’s been (another!) busy month at incident.io HQ: we welcomed Aaron and Anna to our London team and made our first New York hire, Jack (blog coming soon!); we unleashed our inner authors by writing 11 new blog posts; and, we introduced four huge new features (retrospective incidents, post-mortem policies & policy reports, Splunk on-call escalations, and custom incident lifecycles). F-U-N!
Here’s a round-up of some of this month's highlights…
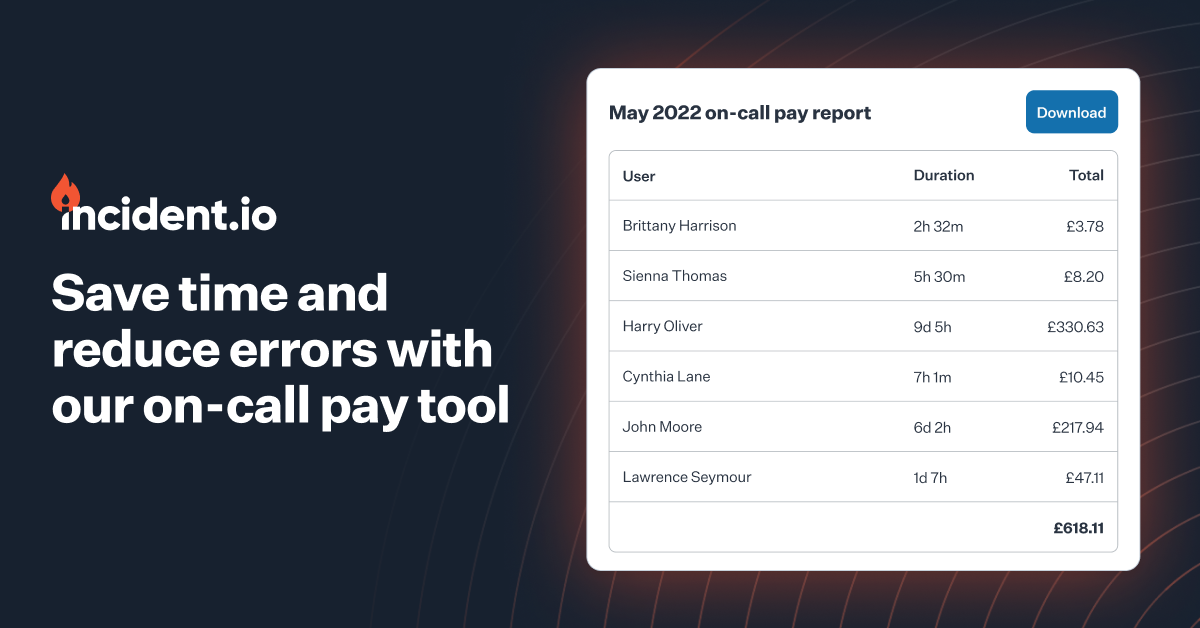
🧮 We’ve made our on-call calculator free to use
We strongly believe that paying for on-call is the right thing to do. Earlier this year, we released our on-call calculator, helping engineering leaders to quickly and accurately work out who is owed what for time spent on-call.
This month we’ve taken it a step further, making the calculator free for everyone. Sign in with Slack, connect to PagerDuty and configure your pay rules. We’ll take it from there, so you can create monthly pay reports ready to go in one click.
Visit our on-call page to get started. Not all heroes wear capes 🦸
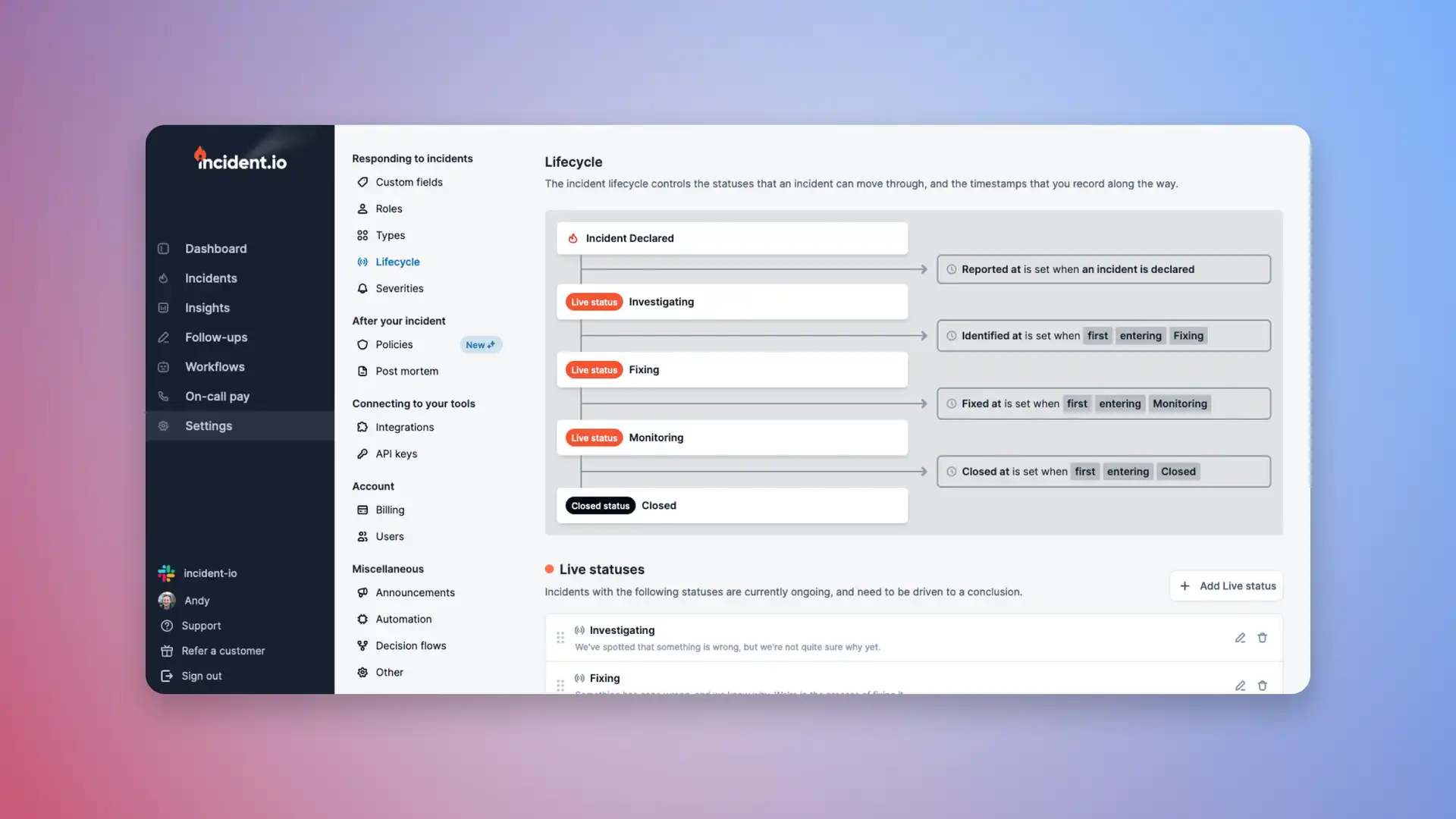
🚴♀️ Customise your incident lifecycle
A consistent lifecycle can help you track and understand your incidents' progress. incident.io provides you with four default statuses: Investigating, Fixing, Monitoring and Closed. But we know every organization does things differently, so we’ve made some changes. Now you can:
- Customise your incident statuses to reflect how you think about incidents in your organization.
- Set timestamps for each of your statuses (manually or automatically), helping you to store structured data about your incidents which you can use for reporting and analysis.
You can read more in our changelog.
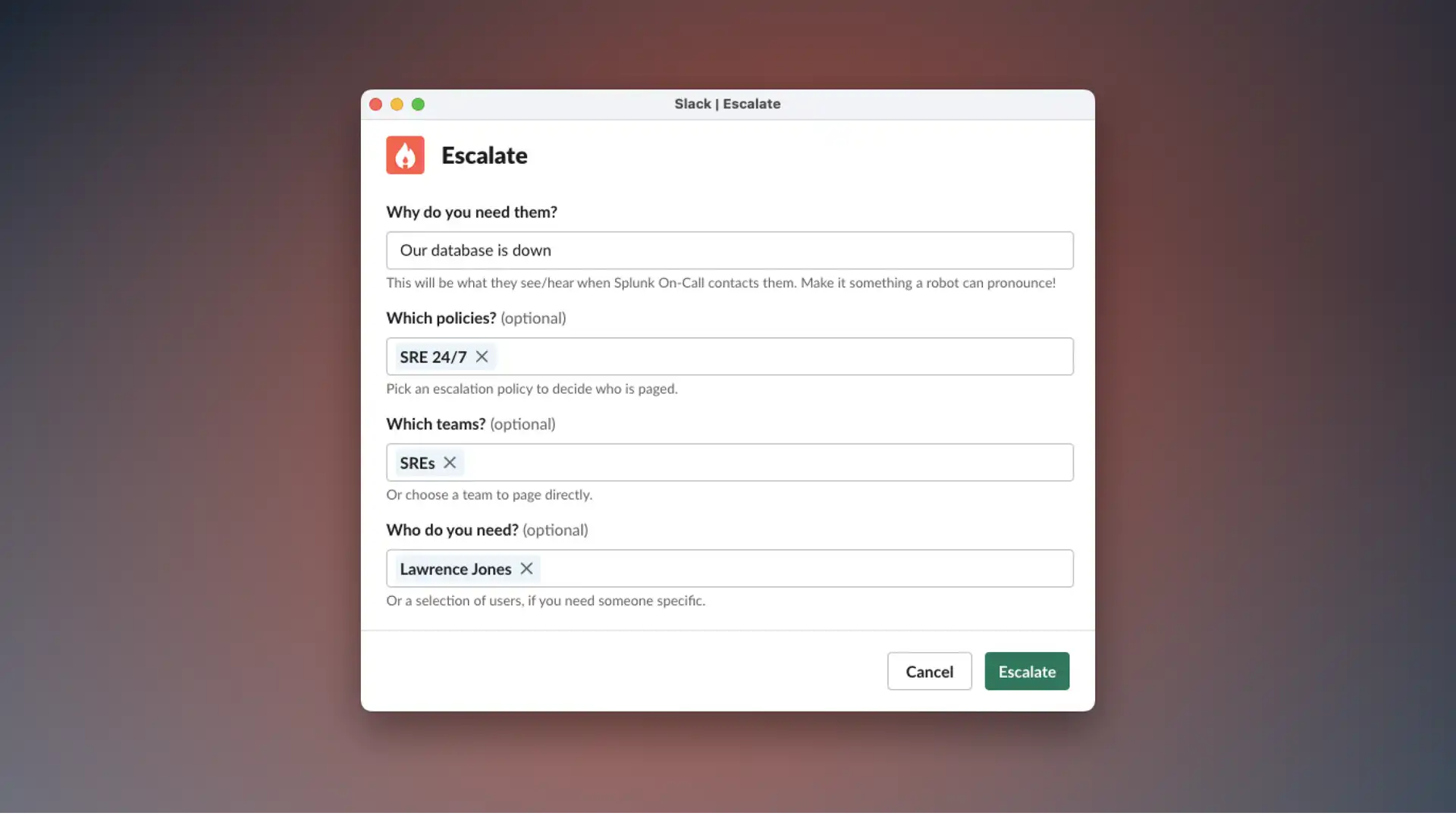
📞 Escalating with Splunk On-Call
Sometimes, you need to call in a lifeline and phone-a-friend during an incident. This can be done directly from slack via /inc escalate. We already support PagerDuty and Opsgenie, but this month we went even further and added support for Splunk On-Call 🎉
Let us know who you need, which team they belong to or which policy to escalate to, and we’ll manage the rest. Your incident channel will be updated with real-time notifications and acknowledgements.
As always, read more about Splunk On-Call in our changelog.
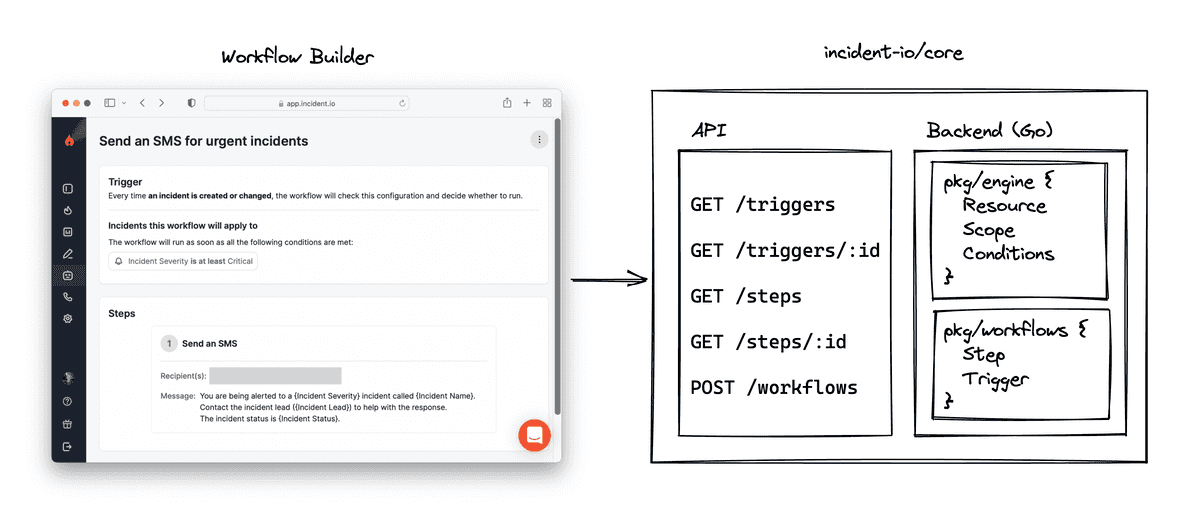
🔥 Hot off the press
Behind the scenes at incident.io: building workflows
Lawrence wrote a blog post about how we built one of our most powerful features: workflows. Think F1 Drive to Survive, but a little nerdier - it’s a behind-the-scenes tell-all, revealing the inner workings of the engineering team here at incident.io. Find out how our core workflow concepts were built, how the code was structured to make development easy, and more. A must-read for anyone building workflow-like features into their products, but just as interesting for anyone who enjoys seeing how engineering teams solve a product problem in a real business space. You can find the blog post here.
Mushroom farmer → founder 🍄
This month, Stephen (co-founder and CEO at incident.io) spoke to Ben Henley Smith on the Best Work Podcast. While his school career quiz advised him to become a mushroom farmer (which sounds unlikely, but it’s true), Stephen was confident he wanted to follow a different path.
In his conversation with Ben, he discusses how he discovered the joys of software engineering and ultimately co-founded incident.io. Sharing the lessons he’s learned so far, listen to why prioritisation is the ultimate skill in a post-product market fit company, how to find the balance between data and gut instinct, and much more. A great listen for anyone interested in the start-up journey. Check it out here.
And finally…
👪 Review us on G2 Already using incident.io? We’d love you to review us on G2. Let us know when you’ve submitted your review, and we’ll send you some coveted swag in return!
See related articles

Let's make incident management convenient, shall we?
Welcome to the February 2023 edition of our newsletter.
 incident.io
incident.io
Triages, bulk edits, post-mortem templates and so much more
Welcome to the January 2023 edition of our newsletter.
 incident.io
incident.io
It’s been fun, 2022. Hello, 2023!
Welcome to the December 2022 edition of our newsletter.
 incident.io
incident.ioSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



