Here’s what to focus on when reviewing an incident

Incidents can be a bit noisy.
Especially when it’s one of higher severity, there are a lot of moving parts that can make it difficult to come away with the information you want at a glance. And if you’re someone who isn’t necessarily tapped into the day-to-day of incident response, such as a head of a department or executive, you’ll want to be able to glean the most actionable information in just a few seconds without having to dig through dense documents.
Take this scenario: you’re an executive at a SaaS company who’s just learned of a major breach of your tool that’s causing disruptions to your website. You’ve suddenly been asked to get your investors up to speed on what’s going on and how big the impact might be. It’s unlikely that, in this scenario, you’ll have the time or headspace to dig into an incident dashboard and look around for the information that’s going to help you best explain what’s going on.
So what’s the solution here?
In these scenarios, whether you only have a few minutes to spare in a packed day or if you’re a manager trying to prepare an executive summary for a particularly big incident, there are a few things you can focus on. From potential impact, to timelines and response teams, here’s what you can hone in on to get the most out of your incident review.
1) What’s the incident?
This feels like the most obvious but it bears repeating, if you’re looking for quick information about what’s going on with an incident, take a quick look at what the incident actually is.
While a lot of the times this won’t be particularly revealing (there’s still a lot of work to be done to find a resolution and deduce exactly why it happened in the first place), it’s still a helpful piece of information to know for your own sanity. Especially if you’ve seen a similar incident happen in the past, knowing what the incident is can be a trigger for you to tap someone who you know has dealt with similar issues in the past.
2) Potential impact
This is likely to be one of the most popular tidbits of information, especially for incidents of high or critical severity. What’s the potential impact here and likelihood of impact under various scenarios? While an incident is unfolding, your team might not know exactly how severe the problem is, but how bad could it be?
In these situations, you’re trying to make the best decisions you can under an umbrella of uncertainty. To do this, you need certain parameters to work within. For example, imagine a security incident where someone may have had access to some data they should not have. In this scenario, you don’t need to know exactly what files were accessed. But if you know that they had access to X system, for Y time, then you can make quick assumptions that allow you to make decisions quickly.
3) Timelines
This is another high level but potentially revealing bit of information: how long have systems been affected?
This figure might indicate a few things, such as the complexity of the incident, that can help you make better, and quicker, business decisions. Other timeline related questions you might want to look for answers to are what the team has already tried to resolve the incident and how much longer the incident might take to find resolution.
Again, these pieces of information can make it easier for you to digest how involved you may need to get in the incident response or how heavy a communication plan you may need to develop for any critical business partners.
4) Who’s on the incident response team?
This leans more into logistics but is still important to cover.
Who’s currently working to resolve the incident?
With a dedicated incident management tool, the answer should always be: someone, especially if it’s during off-hours and requires a page. But things do happen and incidents can fall through the cracks.
In instances like these, not seeing someone assigned to an incident can simply be a signal to you to get that incident in front of the appropriate person for resolution. It could also be a signal that your processes might need some stress testing. Why was no one assigned to this incident? Did something go wrong? Was there a glitch in one of our systems? Instances like these can be part of a bigger action plan.
5) What actions are being taken right now
Nothing gives you better peace of mind than knowing exactly what actions are being taken to resolve an incident. Another benefit of having a list of in-progress actions is that you can easily communicate them to any appropriate folks across the org.
It also serves as a bit of a sense check.
Do the actions being taken by your team align with your expectations for an incident of that severity? E.g. is a Critical incident being treated like exactly that?
Need to follow along an incident but don’t have the time? Our Subscription features solves for that
While we all want to be able to follow along every incident to ensure that they’re getting resolved appropriately, the fact is that there isn’t enough time to in day to sit in an incident dashboard and wait for updates.
We knew that this was an issue so we came up with a resolution. Now, thanks to our Subscriptions feature, you can get alerts for incidents you care about most via Slack DM, to your inbox, or via an SMS.
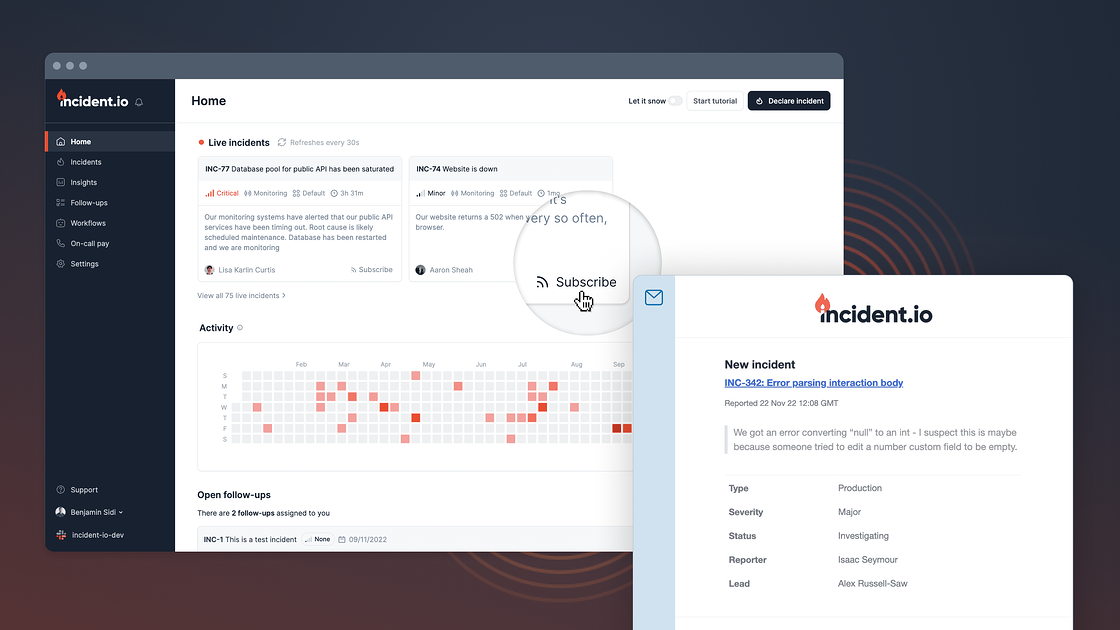
This feature allows you to stay up-to-speed on what’s going on with a particular incident without disrupting or pausing your workflows. You can even set up auto-subscriptions to incidents based on specific criteria. Do you always want to be looped into critical severity incidents related to data breaches? Or incidents that affect a certain number of customers? There’s an endless amount of use cases!
Go to user preferences in your dashboard to get set up.

See related articles

The post-mortem problem
Post-mortems are one of the most consistently underperforming rituals in software engineering. Most teams do them. Most teams know theirs aren't working. And most teams reach for the same diagnosis: the templates are too long, nobody has time, nobody reads them anyway.
 incident.io
incident.io
Keeping it boring: the incident.io technology stack
This is the story of how incident.io keeps its technology stack intentionally boring, scaling to thousands of customers with a lean platform team by relying on managed GCP services and a small set of well-chosen tools.
 Matthew Barrington
Matthew Barrington 
Secure access at the speed of incident response
Blog about combining incident.io's incident context with Apono's dynamic provisioning, the new integration ensures secure, just-in-time access for on-call engineers, thereby speeding up incident response and enhancing security.
 Brian Hanson
Brian HansonSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



