Incident management tools for enterprise: Compliance, security & scale
Updated January 19, 2026
TL;DR: Enterprise incident management requires more than SSO and audit logs. True compliance happens when the easiest path for engineers is also the secure path. We eliminate the security-versus-speed tradeoff by automating timeline capture, enforcing Private Incidents for sensitive issues, and providing SOC 2 Type II certified workflows that live natively in Slack. When engineers bypass your incident tool because it's too complex, you create audit gaps and shadow IT risks. PagerDuty's enterprise tier has been reported at $99/user/month, Opsgenie is being sunset in April 2027, and manual coordination between Jira and Slack adds coordination overhead.
Your team just experienced a critical data breach affecting 50,000 customer records. Three months later, during your SOC 2 Type II audit, the auditor asks for a complete timeline. You have nothing. The engineers coordinated the response in a private Slack DM group because the official incident tool doesn't support restricted channels, leaving no audit trail for the investigation.
This scenario repeats across enterprises daily. Organizations pursuing SOC 2 must meet Common Criteria controls including Communication and Information (CC2), Control Activities (CC5), System Operations (CC7), and Risk Mitigation (CC9). But compliance isn't achieved by locking down tools until they're unusable. It's achieved by making the compliant path the path of least resistance. The right platform ensures engineers naturally work within auditable systems because those systems are faster and easier than workarounds.
This guide evaluates enterprise incident management platforms against the rigorous demands of security, compliance, and scale, showing how modern automation satisfies both the CISO and the SRE.
What defines enterprise-grade incident management
Enterprise incident management software is not just alerting. It's centralized governance, tracking, and compliance automation for large-scale operations where a single incident can affect millions of users and trigger regulatory reporting requirements.
If you're running a 500+ person organization, here are the non-negotiables:
Scale and reliability: You need 99.99% uptime guarantees with hot standbys. When your primary infrastructure fails, your incident coordination tool cannot fail simultaneously. We host transactional data processing to ensure EU data residency and high availability.
Access control: SCIM (System for Cross-domain Identity Management) automates user provisioning so when employees leave, their incident access is automatically revoked. User permissions sync with your Identity Provider, eliminating security gaps from stale credentials.
Observability integration: Deep two-way sync with Datadog, Prometheus, and New Relic reduces context switching during critical incidents.
Total Cost of Ownership (TCO): License fees are only part of the equation. Calculate training costs, integration maintenance, and coordination overhead. Engineer time spent assembling teams and switching between tools adds up quickly at $150/hour loaded cost.
"The separation of functionality between Slack and the website is extremely powerful. This gives us the ability to have rich reporting and compliance controls in place without cluttering the experience and the workflow for the incident responders working to solve the incident during the live phase." - Joar S on G2
Core compliance requirements: SOC 2, GDPR, and HIPAA
SOC 2 Type II certification
SOC 2 Type II evaluation covers access management, system monitoring, incident response, and data backup processes, with auditors looking for evidence that controls work day in and day out. Type I is a snapshot of control design at a single point in time. Type II proves controls worked effectively over a period, usually 6-12 months.
You need an incident management platform that provides:
- Immutable documentation: Evidence is the currency of a SOC 2 Type 2 audit, with each policy item tied to concrete outputs including IAM logs for MFA, ticket IDs for change approvals, and audit trails for incidents.
- Incident reporting mechanisms: Management is required to include specific information about incidents that occurred as a result of a failure in controls or upon occurrence resulted in the company not being able to meet service commitments.
- Automated timeline capture: Manual post-mortem reconstruction creates audit gaps. We capture every Slack message, role assignment, and decision point automatically, building timelines auditors can export without gaps.
GDPR and data sovereignty
GDPR is a comprehensive data protection law to safeguard privacy rights of individuals within the EU and EEA, where data residency ensures personal data is stored and processed within specific geographic locations.
Data residency controls: GDPR mandates strict data residency requirements, ensuring personal data of EU residents is stored and processed within specific geographic locations. You should conduct a data mapping exercise to understand where personal data is stored and review data processing agreements to include specific provisions relating to data residency.
Breach notification and response: You must notify the relevant supervisory authority within 72 hours of becoming aware of a data breach that poses risks to individuals' rights and freedoms. When the breach is likely to result in high risk, you must also inform affected data subjects without undue delay. Your incident platform must enable rapid documentation workflows that meet this timeline, with organizational measures including least-privilege access, enhanced monitoring, and incident response procedures.
HIPAA requirements for healthcare incidents
HIPAA requires healthcare organizations to ensure the confidentiality, integrity, and availability of protected health information, making it necessary to monitor and track both authorized and unauthorized access to PHI.
Audit requirements: You must retain audit log records for six years, tracking electronic PHI access in tamper-resistant systems with encrypted backup storage. Your audit logs must record user activities in applications including files opened, records created or edited, and events initiated by users. The HIPAA Security Rule requires hardware, software, and procedural mechanisms that record and examine activity in systems containing ePHI, enabling you to identify risks from unauthorized access, impermissible disclosures, and suspicious activities.
Security and governance features that matter
Private incidents for sensitive issues
We built Private Incidents so only people in the incident channel have access to it. If you create an incident as private from the start, this includes the incident creator and anyone they actively invite. If you turn a public incident private, this includes anyone who was on the public-turned-private channel and anyone invited hereafter. Private incidents are undiscoverable by users who are not already in the channel.
Critical caveat for governance: incident.io Workspace owners and Slack Workspace owners have access to all private incidents, even those they're not actively invited to. This ensures compliance oversight and prevents incidents from becoming completely invisible during audits.
If someone outside a private incident channel is paged, they can request access via a placeholder page, which sends a message to the private incident channel asking for confirmation or denial. If you deny access, the user is not informed, and an individual user can only request access every 15 minutes.
This feature is essential for security incidents, HR investigations, legal matters, and data breaches where limiting visibility protects both the investigation and regulatory compliance.
Role-based access control (RBAC)
We use predefined roles that build upon each other, with three defaults: Regular User, Administrator, and Owner. Viewers can view and declare incidents. Responders can additionally participate in incident response. Admins can modify organization settings and owners can do everything.
You can create custom roles with specific permissions and assign those to users, with permissions granted in addition to base role permissions. Examples include restricting workflow creation to admins or approving private workflows for permission escalation. SCIM integration automatically provisions users and manages their permissions, with users created when assigned in your Identity Provider and permissions managed automatically without manual role assignment.
Data residency and audit logs
Data residency: For enterprises operating in regulated industries or geographies, where data lives matters. We store data according to EU data residency compliance for GDPR requirements.
Audit logs: Organizations can track setting changes with audit logs going to Datadog, providing the flexibility and oversight needed for compliance. Immutable audit trails capture who changed what configuration, who accessed what incident, and when permissions were modified.
"We can allow all business units to customize workflows for their specific process while having a consistent process overall across the company and we can keep track of any setting changes with audit logs going to DataDog. It gives us the flexibility and oversight we need." - Verified User on G2
Managing scale: Reliability, support, and rapid onboarding
Support velocity that matches enterprise urgency
Enterprise teams cannot wait three days for a ticket response when production is down. PagerDuty's Professional plan offers email-only support, with live chat restricted to Premium Support customers. This is unacceptable for mission-critical infrastructure.
We provide shared Slack channels with customers for real-time support. Customers report bugs fixed within hours and feature requests implemented in days rather than quarters. This support velocity is itself a security feature because critical bugs during incidents cannot wait.
"incident.io tech support is fantastic. When you have a problem, someone from incident.io immediately opens a chat with you in the slack channel, email, or anywhere else to solve the problem immediately." - Tiago T. on G2
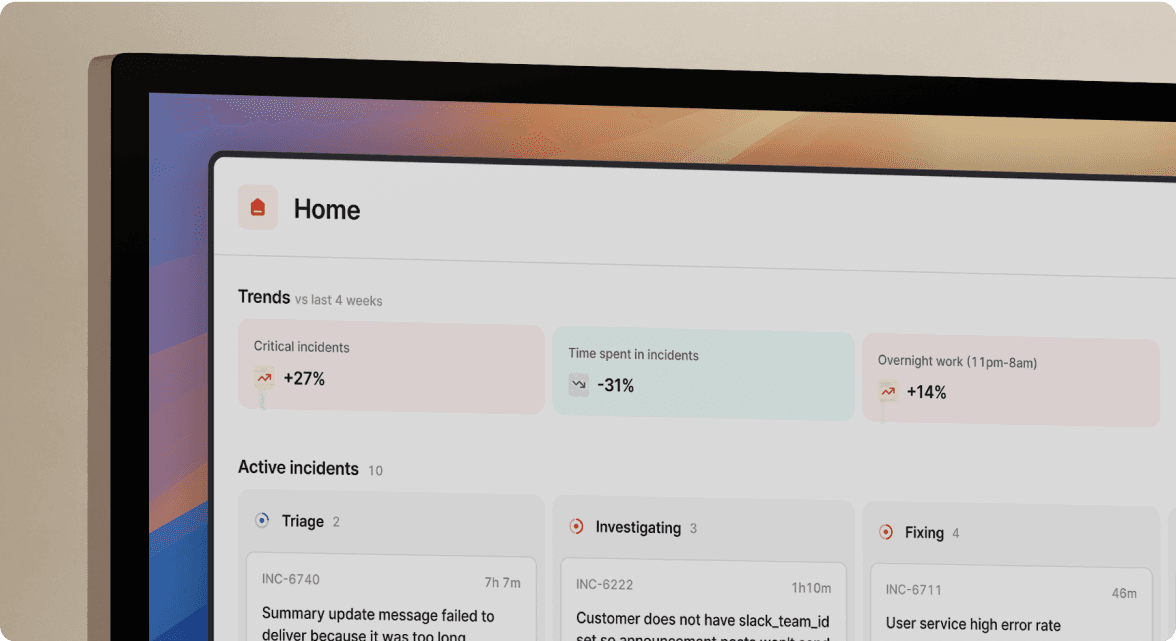
Reliability patterns through insights dashboards
Our Insights dashboard surfaces systemic issues like "Payment Service fails every Tuesday" or patterns showing which services drive the most incidents. You can use these patterns to inform reliability investments and prove to leadership that you're improving MTTR quarter over quarter, not just getting faster at apologizing. This data answers the question your VP of Engineering keeps asking: "Are we getting better at incidents?"
Onboarding new on-call engineers rapidly
When incident.io was introduced at Netflix, rapid organic adoption was seen because the tool was easy to pick up without much guidance, with its intuitive design allowing users to discover features as they used it. This reduces onboarding friction and ensures new engineers can participate effectively in their first incident within days.
"The ease of use and the interface. It's so easy that for reporters across the company it's basically no training and for responders or users customizing workflows it's minimal." - Verified User on G2
The SRE experience: Why usability drives compliance
The shadow IT compliance risk
If a tool is hard to use with high cognitive load, your engineers will bypass it. This breaks compliance. When PagerDuty requires opening a web UI, then manually creating a Slack channel, then copying alerts, engineers take shortcuts. They create DM groups. They skip documentation. They lose audit trails.
The biggest threat to your compliance isn't technical controls but adoption. A perfectly secure tool that nobody uses creates more risk than a slightly less feature-rich tool with 100% adoption.
Slack-native workflows ensure complete capture
We eliminate coordination overhead entirely by unifying the workflow in Slack, with no manual synchronization, no timeline reconstruction, and no documentation archaeology. Because the entire incident lifecycle happens in monitored Slack channels with dedicated incident IDs, compliance capture is automatic.
When alerts fire, we automatically create dedicated incident channels, pull in on-call responders, start capturing timelines, and kick off workflows without engineers leaving chat. Every message, every role assignment, every escalation is captured automatically.
Automated timeline capture prevents audit gaps
Scribe transcribes incident calls and looks to actively pull key moments from the call transcript including important decisions, eliminating the need for a dedicated note-taker. When someone mentions a deployment correlation, Scribe notes it automatically. This real-time documentation means the audit trail builds itself.
Manual post-mortem reconstruction from Slack scroll-back takes 60-90 minutes and introduces errors. Automated generation takes 10-15 minutes and is 80% complete without human input, using captured timeline data.
"I really like its integration with Slack, quickly and visually alerting us to an issue. The possibility of customization and the alerts about actions to be completed and executed is very guiding. It helps a lot on focusing the understanding and emergency solution of the problem, giving us the condition to do a post-mortem associated with the incident later." - Cassio F on G2
AI automation reduces toil and MTTR
Our AI SRE assistant automates up to 80% of incident response, identifying likely changes behind incidents and suggesting next steps based on past incidents. The AI can open pull requests directly in Slack and pulls metrics and logs into incident channels, reducing the manual work that typically slows resolution.
Top enterprise incident management tools compared
| Feature | incident.io | PagerDuty | Opsgenie | Jira Service Management |
|---|---|---|---|---|
| SOC 2 Type II | ✓ Certified | ✓ Certified | ✓ Certified | ✓ Certified |
| Data Residency | EU (Belgium/Netherlands) | Multiple regions | Not specified | Not specified |
| Private Incidents | ✓ Native | Limited | Manual | Manual |
| Slack-Native | ✓ Full workflow | Notifications only | Notifications only | Integration only |
| Enterprise Pricing | Contact sales | Reported $99/user/month | Being sunset April 2027 | Bundled with JSM |
| SCIM/SSO | ✓ Pro+ plans | ✓ Enterprise only | ✓ Available | ✓ Available |
| Automated Timeline | ✓ Built-in | Manual | Manual | Manual |
| Support Model | Shared Slack channels | Email for Pro tier | Standard tickets | Standard tickets |
PagerDuty: Expensive incumbent with feature gating
PagerDuty's Digital Operations (Enterprise) tier has been reported at $99 per user/month by IT procurement firms, with critical enterprise features like advanced analytics, automation, and comprehensive security controls gated behind this highest tier. Official PagerDuty pricing requires contacting sales for Digital Operations quotes, which vary by organization. For a 500-person engineering organization, annual costs can reach $594,000 before add-ons.
AI features start at $699/month plus usage-based costs, and many teams find they need multiple add-ons substantially increasing actual costs. The platform is fundamentally web-first with Slack notifications bolted on, requiring manual coordination between tools. PagerDuty excels at alerting and on-call scheduling, but coordination happens outside the platform.
Opsgenie: Sunset risk eliminates viability
Atlassian announced that Opsgenie will no longer be available for new purchases or trials starting June 4, 2025, with end of support on April 5, 2027, and all Opsgenie data will be deleted after this date. Access to Opsgenie will be completely shut down and any un-migrated customer data will be deleted on the end of support date.
Any organization evaluating Opsgenie today faces mandatory migration in less than two years. If you're using the JSM-bundled version, you'll lose access even sooner in October 2025. This sunset creates immediate risk and uncertainty.
Jira Service Management: Ticket-first, not real-time
Jira Service Management provides an ITIL compliant incident management workflow suitable for IT service desk operations, but it's fundamentally ticket-first architecture. There's no instant war room button on Slack for JSM, and the Slack channel must be linked to the incident for actions to work.
Manual coordination between Slack and Jira requires context switching that adds friction during time-critical responses. While JSM automatically generates incident timelines, this happens within the Jira interface, not where engineers are naturally coordinating in Slack.
For detailed migration guidance, we provide tools to make migrating from PagerDuty easier and tools to make migrating from Opsgenie easier before the 2027 sunset deadline.
How incident.io unifies enterprise security with DevOps speed
The false choice between security and speed dissolves when the compliant path is also the fastest path. We achieve this through architectural decisions that make governance automatic rather than manual.
Private incidents for sensitive issues: Security breaches, HR investigations, and legal matters require restricted visibility. Private incidents ensure only invited participants can access sensitive channels, while workspace owners retain oversight for audit purposes. This balances operational security with governance requirements.
Service Catalog for instant context: Our Catalog automatically surfaces service ownership, dependencies, runbooks, and recent deployments within incident channels. Engineers get the context they need without leaving Slack, reducing coordination overhead while ensuring complete documentation.
Status pages for automated communication: Internal and external status pages integrate directly with incident workflows, updating automatically when incidents are declared and resolved. This eliminates the common problem of engineers forgetting to update status pages during chaos, then facing customer complaints hours after resolution.
Proven at enterprise scale: We enable 10,000+ responders at over 600 companies including Netflix, Etsy, monday.com, Intercom, and Skyscanner to streamline, resolve, and learn from every incident. Netflix's evaluation process led to adoption because the platform checked all their boxes, and within four months 20% of engineering teams were using the tooling, reaching over 50% adoption six months later.
"The intuitive design, overall ease of use and stellar customer relationship experience has made me an avid fan of this product. While most companies these days are boasting about their use of AI, incident.io to me stands out about how deliberately they use AI." - Dennis P on G2
Choose tools where usability drives compliance
Enterprise incident management is not about choosing between security and speed. You need platforms where security automation enables speed. When timeline capture is automatic, audit trails build themselves. When workflows live in Slack where engineers naturally coordinate, adoption reaches 100%. When Private Incidents restrict sensitive information while maintaining oversight, compliance and operational security coexist.
The organizations handling incidents most effectively are not using the most complex tools. They're using tools where the path of least resistance for engineers creates the audit trail CISOs require.
Book a demo to see how we handle enterprise security requirements including Private Incidents, RBAC, and compliance-ready timelines. Or start a free trial to run your first incident in Slack and experience the difference between Slack-native workflows and tools that treat chat as an afterthought.
Key terminology
SOC 2 Type II: Security certification requiring immutable audit trails, access controls, and documented incident response procedures, with auditor verification that controls worked effectively over time rather than just existing on paper.
Data Residency: The physical or geographic location where an organization's data is stored, critical for GDPR compliance and other regulatory requirements mandating specific storage locations.
SCIM (System for Cross-domain Identity Management): Open standard protocol that automates user provisioning and deprovisioning, syncing user lifecycle management between Identity Providers and SaaS applications to eliminate stale credentials.
Private Incidents: Restricted-access incident channels where only explicitly invited participants can view sensitive information, used for security breaches, HR matters, and legal investigations requiring limited visibility.
MTTR (Mean Time To Resolution): The average time from when an incident is detected to when it is fully resolved, used as a key reliability metric to measure incident response effectiveness.
RBAC (Role-Based Access Control): Security model that restricts system access based on user roles within the organization, with permissions assigned to roles rather than individuals to simplify access management at scale.
Coordination Overhead: The time spent assembling teams, finding context, and synchronizing information across tools during incident response, typically consuming significant time per incident before troubleshooting begins.
FAQs

See related articles

The post-mortem problem
Post-mortems are one of the most consistently underperforming rituals in software engineering. Most teams do them. Most teams know theirs aren't working. And most teams reach for the same diagnosis: the templates are too long, nobody has time, nobody reads them anyway.
 incident.io
incident.io
Keeping it boring: the incident.io technology stack
This is the story of how incident.io keeps its technology stack intentionally boring, scaling to thousands of customers with a lean platform team by relying on managed GCP services and a small set of well-chosen tools.
 Matthew Barrington
Matthew Barrington 
Secure access at the speed of incident response
Blog about combining incident.io's incident context with Apono's dynamic provisioning, the new integration ensures secure, just-in-time access for on-call engineers, thereby speeding up incident response and enhancing security.
 Brian Hanson
Brian HansonSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



