Incident management trends 2026: The shift to AI, chat-native, and secure workflows
Updated January 30, 2026
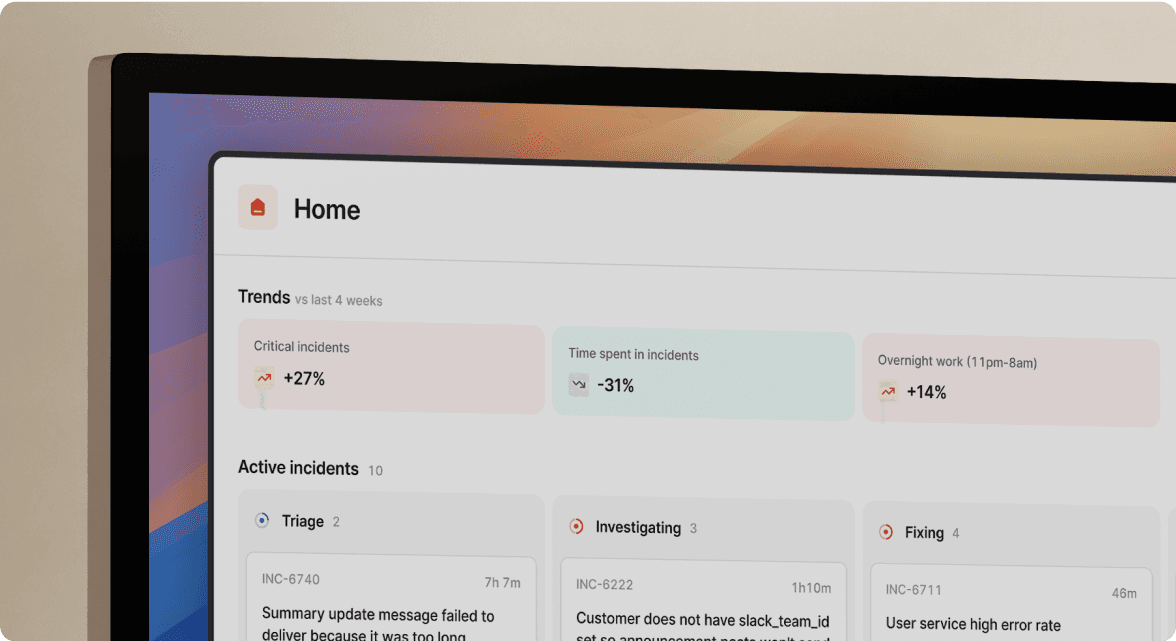
TL;DR: By 2026, incident management shifts from reactive alerting to proactive, AI-driven reliability platforms. The winners leverage autonomous AI to automate up to 80% of incident response, embed security controls (private incidents, granular RBAC) directly into chat platforms, and auto-generate compliance evidence. incident.io leads this convergence with Slack-native workflows, AI SRE capabilities, and security-first architecture that eliminates the 15-minute coordination tax and hundreds of hours in manual audit prep.
The state of incident management in 2026
The incident management industry faces its biggest inflection point since the rise of DevOps. On March 4, 2025, Atlassian announced the Opsgenie sunset with End of Sale effective June 4, 2025, and End of Support on April 5, 2027, forcing thousands of engineering teams to re-evaluate their entire incident response stack. This isn't just vendor consolidation. It exposes deeper frustrations with legacy incident management tools.
Engineering teams face three compounding pressures:
- Tool sprawl kills MTTR. When alerts fire in PagerDuty, coordination happens in Slack, tickets get created in Jira, and post-mortems live in Confluence. Research from the University of California, Irvine shows it takes 23 minutes and 15 seconds on average to regain focus after significant interruptions. Teams lose 15 minutes per incident to coordination overhead before troubleshooting starts.
- CISOs drown in manual compliance work. For ISO 27001, self-managed programs consume 550-600 hours annually on evidence collection. SOC 2 audits require reconstructing timelines from fragmented sources (Slack exports, PagerDuty logs, Zoom transcripts, handwritten notes), risking human error that causes audit findings.
- AI hype everywhere, real utility rare. Most vendors slapped "AI-powered" labels on log summarization without delivering measurable toil reduction. Engineers need AI that acts, not just AI that writes text.
The 2026 trend isn't incremental improvements. We're watching a fundamental architectural shift to platforms that are chat-native, AI-driven, and security-first by default.
Trend 1: Agentic AI and the rise of the AI SRE
The AI landscape splits into two camps: AI washing (vendors adding ChatGPT wrappers to existing products) versus Agentic AI (autonomous systems that take action).
Agentic AI systems operate as autonomous agents within SRE ecosystems. Unlike passive AI assistants that suggest actions upon request, these agents perceive their environment, reason, plan, and execute multi-step tasks independently to achieve reliability goals. The fundamental shift is from human-in-the-loop analysis to human-on-the-loop supervision. The agent becomes the first responder.
What agentic AI does during incidents
An AI SRE acts as the initial recipient of all alerts. It autonomously correlates related signals, suppresses duplicates, and enriches the primary alert with contextual data (recent code changes, related infrastructure events, service dependencies). It only escalates to a human engineer when it has high-confidence assessment of a critical incident requiring human judgment.
Datadog's Bits AI SRE demonstrates this evolution. Once Bits identifies a code-related root cause, the AI Dev Agent proposes a fix and generates a pull request. Engineers review and merge the PR directly from Slack. This is fundamentally different from "here are some related logs" summarization.
incident.io's AI SRE embeds directly into Slack workflows. When an alert fires, the AI SRE can automate up to 80% of incident response, identifying the likely change behind incidents, suggesting next steps based on past incidents, and pulling metrics and logs into Slack without requiring engineers to context-switch to Datadog or Grafana dashboards.
The agentic AI checklist
When evaluating AI capabilities in 2026, ask:
- Does the AI take action or just write text? Generating fix PRs, rotating credentials, and executing runbook steps equals Agentic. Summarizing logs equals Generative (useful but not autonomous).
- Does it handle multi-step workflows autonomously? Real agents chain tasks: correlate alerts, identify root cause, pull related code changes, suggest fix, open PR. Co-pilots help you do one task at a time.
- What's the precision and recall? incident.io's AI SRE achieves validated performance in root cause identification, automating up to 80% of incident response. Vendors hiding metrics are hiding underwhelming results.
- Is the AI secure and auditable? For CISOs, AI that trains on customer data without consent or lacks audit trails introduces compliance risk. incident.io's AI architecture uses encrypted data at rest and in transit, respects access controls (Private Incidents remain private from AI training), and provides audit logs of AI actions.
"incident.io brings calm to chaos... It's the source of truth for incidents we've always needed." - Braedon G. on G2
The 2026 winner is the vendor whose AI measurably reduces MTTR by handling the first 80% of incident response autonomously, letting engineers focus on the complex 20% requiring human creativity.
Trend 2: Chat-native platforms replace web-first dashboards
The dashboard era is ending. Web UIs are becoming secondary interfaces for post-incident analysis, not primary incident response tools. The future of incident management is chat-native, where the entire lifecycle (declaration, coordination, resolution, post-mortem) happens inside Slack or Microsoft Teams.
Why chat-native wins
Context switching costs engineers 9.5 minutes on average to return to productive workflow, according to research from Qatalog and Cornell. During high-stress 2 AM incidents, asking engineers to open PagerDuty, create a Jira ticket, update Confluence, and coordinate in Slack is cognitive overload.
Teams using true Slack-native platforms become operational in 3-5 days versus PagerDuty's typical 2-6 week configuration. There's no training required. If you know how to use Slack, you know how to declare an incident.
What "truly native" means
PagerDuty and Opsgenie offer Slack integrations that enable users to trigger, acknowledge, escalate, and resolve incidents without leaving Slack. However, incident.io takes a Slack-native approach where the entire incident lifecycle lives in Slack through deep slash command integration. The web UI exists primarily for analytics and configuration rather than real-time response.
Slack integration (PagerDuty approach): The web UI is primary. Slack receives notifications and allows limited actions (acknowledge alert). Complex workflows (assigning roles, updating status pages, managing follow-ups) require opening the web dashboard. According to PagerDuty's integration documentation, users can take action on incidents without leaving Slack, but the platform remains fundamentally web-first with Slack as an interface layer.
Slack-native (incident.io approach): The incident lifecycle happens in Slack through deep slash command integration. You declare incidents with /inc declare, assign roles with /inc assign, escalate with /inc escalate, and resolve with /inc resolve. The web dashboard exists for Insights analytics and administrative configuration, not real-time response.
incident.io's architecture means that when a Datadog alert fires, the platform auto-creates a dedicated incident channel (#inc-2847-api-latency-spike), pulls in the on-call engineer, populates service context from the Catalog, and starts capturing the timeline automatically. Everything needed is in one Slack channel. No browser tabs. No "where do I go next?" decision fatigue.
"The slack integration makes it so easy to manage the incident... there are tons of ways to customize the decisions and automate communication." - Gregorio B. on G2
The mobile advantage
During incidents that wake you at 3 AM, you're responding from your phone. Slack and Microsoft Teams have excellent mobile apps. PagerDuty's mobile app is rated 4.8 stars on iOS, but it's still a separate app to open, remember credentials for, and navigate. incident.io works through the Slack app already on your phone's home screen, with notifications already configured.
ChatOps connects people, tools, process, and automation into a transparent workflow in a persistent location. The transparency tightens the feedback loop, improves information sharing, and enhances team collaboration during incidents.
Trend 3: Compliance automation becomes a standard feature
For CISOs evaluating incident management tools in 2026, the question isn't "does it help us respond faster?" It's "does it help us pass audits without manual evidence collection?"
The manual compliance tax
ISO 27001 self-managed programs consume 550-600 hours annually on evidence collection tasks. SOC 2 audits require demonstrating consistent, repeatable incident response processes. When processes are ad-hoc (different teams using different methods), auditors question control effectiveness, increasing audit scope and cost.
The traditional approach involves reconstructing incident timelines from Slack exports, PagerDuty logs, Jira tickets, Zoom transcripts, and handwritten notes three days after the incident when details are fuzzy and witnesses have moved on. One CISO described this as "solving a crime scene without photos."
Private incidents and granular RBAC
The biggest security gap in legacy incident tools is the inability to isolate sensitive incidents. When a zero-day vulnerability or potential data breach occurs, you cannot accidentally expose PII, vulnerability details, or confidential remediation plans in public Slack channels visible to 200 engineers.
incident.io's Private Incidents feature addresses this directly. You can limit incident visibility to specific users or teams, maintain separate audit trails for security versus operational incidents, and enforce granular RBAC via SAML/SCIM integration with identity providers like Okta.
Automated audit evidence generation
Modern platforms turn every incident into audit-ready evidence without manual effort. incident.io captures:
- Who did what, when: Every
/inccommand, role assignment, and participant action with timestamps - Communication trail: All Slack messages in incident channels, status page updates, customer notifications
- Decision context: Scribe AI transcribes incident calls via Google Meet or Zoom, extracting key decisions during active incidents
- Follow-up accountability: Action items automatically flow into Jira or Linear with assignment and due dates tracked
When it's time for SOC 2 surveillance audits, you export incident data as CSV or JSON. The evidence package shows auditors exactly who was notified when, what actions were taken, and how you ensured consistent processes across all incidents.
incident.io is SOC 2 Type I compliant with ongoing interest toward Type II certification, meaning automated audit trails, granular access controls, and data residency in EU regions (Belgium and Netherlands) that satisfy compliance requirements without hundreds of hours in manual evidence collection sprints.
"incident.io allows us to focus on resolving the incident, not the admin around it. Being integrated with Slack makes it really easy, quick and comfortable to use for anyone in the company, with no prior training required." - Andrew J. on G2
Compliance feature checklist
When evaluating tools in 2026, CISOs should verify:
| Requirement | What to verify | incident.io capability |
|---|---|---|
| SOC 2 certification | Download certification report | SOC 2 Type I certified, Type II in progress |
| GDPR compliance | Review Data Processing Agreement | GDPR compliant with EU data residency |
| Private incidents | Test RBAC enforcement in demo | Granular access controls via SAML/SCIM |
| Audit trails | Export sample incident logs | Immutable timelines exportable as CSV/JSON |
| Identity integration | Confirm SAML/SCIM support | Full integration with Okta, Azure AD |
Trend 4: Observability and incident response convergence
Monitoring tools (Datadog, Prometheus, Grafana) and incident management platforms are converging. Engineers shouldn't leave Slack to see a Datadog graph. The context should come to them.
incident.io's Datadog integration automatically pulls information about monitors that triggered escalation directly into incident channels. When you join an incident, you immediately see the triggering monitor name with a link, up to 500 characters of the monitor body (including runbooks), and the Alert Priority. The monitor is recorded as an attachment on the incident homepage and listed in the Timeline.
If you paste a link to Datadog snapshots, Slack unfurls the image. If you pin that message, incident.io adds the linked image to your timeline. This eliminates the "let me find that dashboard link" delay during active incidents.
incident.io's Service Catalog surfaces critical context automatically. When an incident fires for a service, the incident channel populates with owner information, dependency map, recent deployments, and runbook links without manual lookup. The Timeline feature captures everything chronologically: alerts, Datadog/Grafana graphs pinned in Slack, Slack messages and discussions, /inc commands, Scribe call transcriptions, and resolution steps.
This unified view means post-incident reviews don't require reconstructing "what happened when" from memory. The timeline is the source of truth, automatically generated as the incident unfolds.
Trend 5: Proactive prevention with AI-driven insights
The most advanced teams now move from reactive incident response to proactive reliability engineering using AI-driven pattern recognition.
Traditional post-mortems capture what went wrong after the fact. Modern platforms analyze incident data across months to identify systemic patterns: Which services have the highest incident frequency? Which types of incidents (deploy-related, infrastructure, third-party API) consume the most engineering time? Which teams are experiencing on-call burnout based on after-hours incident frequency?
incident.io's Insights dashboard provides visibility into MTTR trends, incident patterns by severity and service, and on-call readiness metrics. On-call Readiness Insights help teams identify when engineers are under-prepared for their on-call rotation, allowing proactive training before the pager goes off.
Agentic AI doesn't just respond to incidents. It learns from them. When similar incidents occur, the AI SRE surfaces past incidents with comparable symptoms, shows what worked last time, and suggests applying the same fix. This institutional knowledge previously lived in senior engineers' heads. Now it's accessible to junior engineers on their first on-call shift.
Incidents reveal reliability gaps. The question is whether action items get completed or lost in Jira backlogs. Modern platforms automatically create follow-up tasks, assign owners, and track completion rates. incident.io's Jira integration populates tickets with timeline data, so engineers don't manually transcribe incident details into separate tracking systems.
CISOs can measure whether reliability investments are working by tracking: Are follow-up completion rates improving? Is MTTR trending down? Are repeat incidents decreasing? These metrics prove ROI to executives who control budgets.
Evaluating next-gen tools: A buyer's framework for 2026
With the Opsgenie sunset forcing migration decisions, teams need a clear framework for evaluating modern incident management platforms.
The security and compliance check
For CISOs evaluating platforms:
When reviewing incident management tools, verify SOC 2 certification status (Type I or Type II), confirm GDPR Data Processing Agreement availability, test Private Incident RBAC enforcement during demos, export sample audit logs to verify immutability and format options, and validate identity provider integration via SAML/SCIM.
incident.io provides SOC 2 Type I certification with ongoing Type II audit processes, GDPR compliance with EU data residency (Belgium and Netherlands), Private Incidents with granular access controls, immutable timelines exportable as CSV/JSON, and full SAML/SCIM integration with Okta and Azure AD.
The AI utility check
Avoid AI washing by asking:
- Does the AI take autonomous action? Look for fix PR generation, credential rotation, runbook execution. Red flag: "AI summarizes logs" as the only capability.
- What are the precision and recall metrics? Real vendors publish performance data. incident.io's AI SRE automates up to 80% of incident response. Vendors hiding metrics have weak performance.
- Is AI training secure? Confirm the vendor doesn't train models on customer data without consent, verify AI actions are auditable, and ensure AI respects Private Incident access controls.
Gartner defines AIOps as combining big data and machine learning to automate IT operations processes, including event correlation, anomaly detection, and causality determination. AI SRE is more specific, focusing on applying AI to reliability engineering with incident management, observability, capacity planning, and resilience engineering. The key distinction: AIOps correlates events, while AI SRE takes action.
The total cost of ownership check
PagerDuty's pricing opacity is legendary. You see a base price, then discover that on-call scheduling, event intelligence, status pages, and runbook automation are expensive add-ons. The real cost is 2-3× the advertised price.
incident.io uses transparent pricing. The Pro tier is $25/user/month for incident response. On-call management costs an additional $20/user/month. Your real cost is $45/user/month with full capabilities. No surprises. No "call us for a quote" games.
100-person team annual TCO:
incident.io Pro with On-call costs $45/user/month × 100 users × 12 months = $54,000/year. This includes unlimited workflows, custom fields, on-call schedules, Slack + Microsoft Teams support, AI-powered post-mortems, private incidents, custom dashboards, API access, and live chat support.
Compare this to PagerDuty, which requires separate add-ons for features that incident.io includes in the Pro tier.
The adoption and time-to-value check
During POC, verify:
- Time to first incident declared: Can an engineer declare an incident within 5 minutes of onboarding? Chat-native platforms achieve this. Web-first tools require 30+ minute training sessions.
- Training requirements: Does the platform require a 2-day training program or a 10-minute Slack tutorial? incident.io users consistently report "no prior training required" because it feels like using Slack.
- Integration setup time: How long to connect Datadog, Jira, and status pages? Modern platforms offer one-click OAuth integrations. Legacy tools require webhook configuration, API key management, and IT involvement.
"They absolutely nailed the UX... My favourite thing about the product is how it lets you start somewhere simple, with a focus on helping you run incident response through Slack." - Chris S. on G2
Preparing for the future of reliability engineering
The 2026 incident management landscape rewards platforms that eliminate toil through autonomous AI, embed workflows into chat platforms where engineers already work, and automate compliance evidence collection for security-conscious organizations.
Three actions for engineering leaders and CISOs evaluating tools today:
Run a TCO analysis beyond sticker price. Calculate your current spend: PagerDuty licensing + Jira + Statuspage subscriptions + manual labor for audit prep (hundreds of hours annually based on ISO 27001 evidence collection requirements) + context-switching tax (15 min per incident × incidents/month × loaded engineer cost). Modern unified platforms often cost less while delivering more capability.
Test AI utility, not AI marketing. During POC, simulate a real incident. Does the AI identify root cause? Does it suggest a fix? Does it reduce manual work or just add another dashboard to check? incident.io's AI SRE demonstration shows autonomous triage, root cause identification, and fix proposal generation, not just log summarization.
Validate security controls with your CISO. If you're subject to SOC 2, ISO 27001, GDPR, or HIPAA, verify that the platform provides Private Incidents, granular RBAC, immutable audit trails, and certification documentation before signing contracts. incident.io's SOC 2 Type I certification and GDPR compliance address these requirements out of the box.
The Opsgenie sunset is forcing migration conversations. Use this moment to re-evaluate whether your incident management stack reflects 2020 architecture (web-first, manual, compliance as afterthought) or 2026 reality (chat-native, AI-driven, security-first by design).
Try incident.io free and run your first incident in Slack, or book a demo to see AI SRE and Private Incidents in action.
Key terminology
Agentic AI: Autonomous AI systems that independently execute multi-step workflows (triage, root cause analysis, fix generation) versus passive co-pilots that require human initiation for each task.
Chat-native: Platform architecture where the entire incident lifecycle (declaration, coordination, resolution, post-mortem) occurs inside Slack or Teams via deep integration, not just notifications from a web-first tool.
Private incidents: Capability to restrict incident visibility to specific users or teams with granular RBAC enforcement, maintaining separate audit trails for sensitive security incidents versus operational issues.
MTTR (Mean Time To Resolution): Average time from incident declaration to resolution. Modern platforms reduce MTTR by eliminating coordination overhead through automated workflows and AI-assisted triage.
SOC 2 Type II: Security certification demonstrating that a company has appropriate controls in place and that those controls operated effectively over a minimum six-month observation period.
AI SRE: AI agent focused specifically on site reliability engineering tasks including incident response automation, root cause identification, and proactive reliability pattern analysis versus general AIOps event correlation.
FAQs

See related articles

Secure access at the speed of incident response
Blog about combining incident.io's incident context with Apono's dynamic provisioning, the new integration ensures secure, just-in-time access for on-call engineers, thereby speeding up incident response and enhancing security.
 Brian Hanson
Brian Hanson
Everything you need to know about ITIL 5, AI and incident management
We break down ITIL 5's governance framework and what it means for teams using AI in incident response. For incident management, it addresses questions like: Who's accountable when an AI-suggested remediation backfires? How do you audit AI-generated updates?
 Chris Evans
Chris Evans
DevEx matters for coding agents, too
When AI can scaffold out entire features in seconds and you have multiple agents all working in parallel on different tasks, a ninety-second feedback loop kills your flow state completely. We've recently invested in dramatically speeding up our developer feedback cycles, cutting some by 95% to address this. In this post we’ll share what that journey looked like, why we did it and what it taught us about building for the AI era.
 Rory Bain
Rory BainSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



