Introducing SCIM
April 11, 2023

Following the introduction of Security Assertion Markup Language (SAML), we're happy to share that our enterprise users can now also use System for Cross-domain Identity Management (SCIM) to control user access and authorisation to incident.io.
Both SCIM and SAML can be used independently of each other, but they are often used in combination. SCIM complements the authentication capabilities of SAML, by adding automatic provisioning, deprovisioning and authorisation control.
This means that you can now use identity providers like Okta or Google Workspaces to centrally control (1) user access to incident.io and (2) what the users are allowed to do once they are logged-in to the dashboard.
SCIM can also be used in combination with the recent improvements to our role-based access control (RBAC) capabilities. For example, a group in Okta can be both automatically provisioned and automatically assigned the appropriate RBAC role in incident.io, whether the role is a custom role or a base role. You can read more about configuring users permissions here.
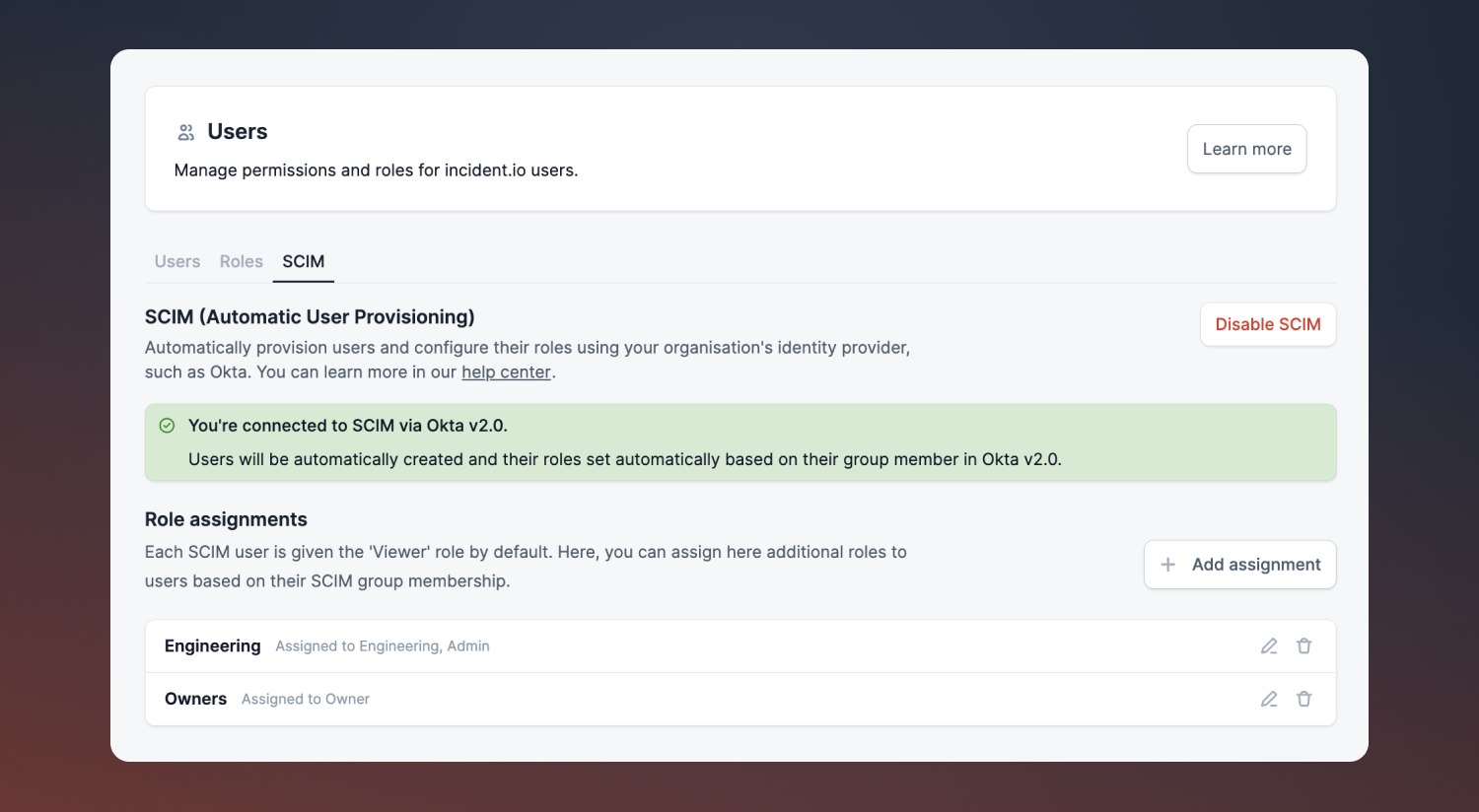
If you use an Identity Provider (IdP) other than Okta SCIM, please get in touch. While we are able to support other IdPs promptly on demand, functionality might be limited.
For more information on how to get started with SCIM, please refer to our help centre article.
🚀 What else we shipped
New
- We've improved post-mortem template variables; you can now add duration metrics as a custom block.
Improvements
- We now hide the 'Live incidents' heading in the dashboard homepage when there are no live incidents.
- We've added a column to the incidents CSV exports that indicates whether or not the incident is private.
- We've made improvements to the Jira Server integration, follow-ups issues now link back to a parent issue that originally triggered the incident.
- We've added
assigneeas an attribute to the follow-up webhooks payload.
Bug fixes
- We are now generating the correct Zoom links for calls that have passwords.
- We've fixed a bug where the API would return a 500 when attempting to delete an API key that doesn't exist.
- We've fixed a bug where the Insights: Readiness charts were not rendering for some organizations.
- We've fixed a bug where the Insights: Workload 'end date' filter was displaying the incorrect selected date.
So good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



