2025 guide to preventing alert fatigue for modern on‑call teams
2025 guide to preventing alert fatigue for modern on‑call teams
Alert fatigue floods on-call engineers with constant notifications, making it easy to miss critical incidents. This guide outlines practical strategies—like centralized data, intelligent grouping, automation, and better scheduling—to cut noise, improve response times, and sustain reliable operations.
Understanding alert fatigue and its impact on on-call teams
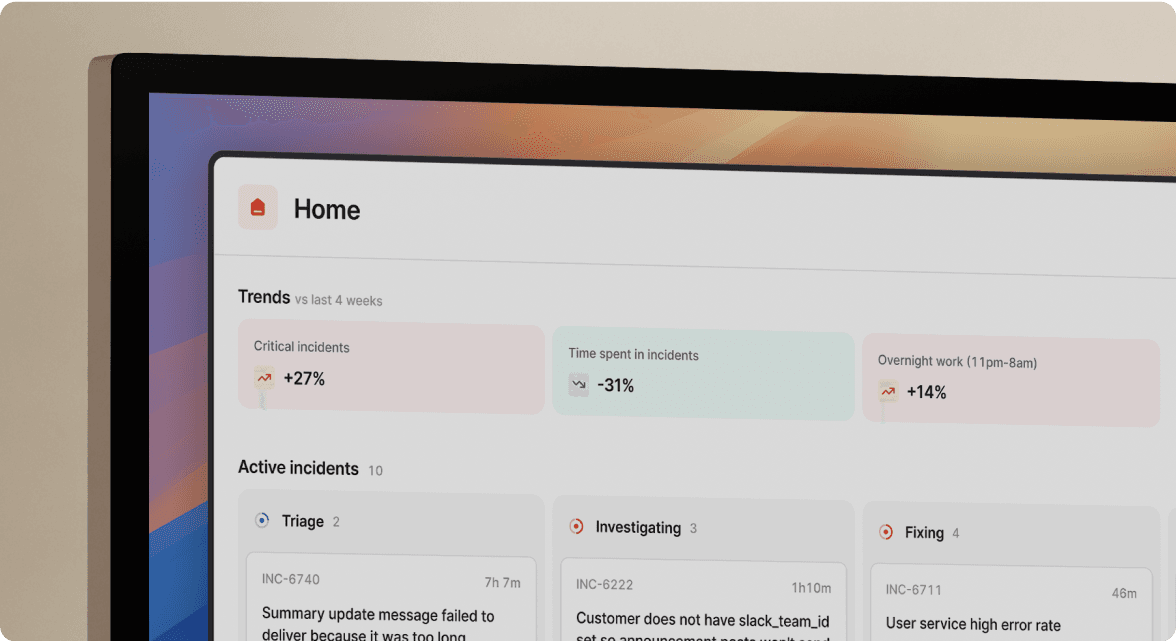
Alert fatigue happens when excessive notifications desensitize engineers, increasing missed critical incidents and slowing response times. As systems grow more complex, monitoring tools multiply and single failures can trigger redundant alerts across logs, metrics, and dependent services, creating distracting noise.
Consequences include longer triage times, lower morale, and faster burnout: engineers spend valuable time filtering alerts instead of resolving root causes, and true emergencies risk blending into routine noise. For example, a microservice failure may generate dozens of notifications for one underlying issue, delaying identification and resolution.
Operational impacts are measurable: higher mean time to acknowledge (MTTA), increased missed incidents, and reduced team capacity for proactive work. Preventing this requires reducing redundant alerts, improving context, and aligning notifications to business impact so engineers can act on what matters.
Centralize incident data to reduce noise and improve accuracy
Centralizing logs, metrics, traces, and alert history is essential for accurate correlation and AI-driven noise reduction. Scattered data prevents meaningful pattern detection and makes de-duplication unreliable.
A unified data pipeline collects disparate sources into a centralized incident management platform, where normalization standardizes formats and correlation algorithms surface relationships between events. Aggregated data enables ML models to establish dynamic baselines, detect anomalies, and reduce redundant notifications.
Modern platforms provide a single pane of glass for operational data; AI-powered alert management can reduce noise by over 90% when models train on comprehensive, centralized data. Benefits also include more accurate root cause analysis, better incident classification, and early detection of systemic issues that fragmented tools miss.
Implement intelligent alert grouping and de-duplication
Alert grouping consolidates related notifications, while de-duplication removes repeats so engineers see unique incidents instead of cascades of noise. Intelligent grouping uses contextual correlation—shared root causes, affected services, or temporal patterns—to cluster alerts into meaningful incidents.
De-duplication leverages dynamic baselines and context to distinguish redundant notifications from legitimate recurring alerts; for instance, multiple alerts in a short window for the same service often represent one incident. Properly configured correlation rules should reflect your architecture to avoid over- or under-grouping.
This approach dramatically cuts noise: over 90% reduction is achievable with intelligent grouping and dynamic baselines, letting engineers focus on real incidents rather than sorting duplicates.
| Metric | Before grouping/de-duplication | After implementation |
|---|---|---|
| Daily alerts per engineer | 200-500 | 20-50 |
| Time spent on alert triage | 3-4 hours | 30-60 minutes |
| Missed critical incidents | 5-10% | <1% |
| Engineer satisfaction | Low | Significantly improved |
The implementation key is tuning correlation rules to your environment: avoid generic algorithms that miss nuanced relationships and overly aggressive grouping that hides distinct issues.
Prioritize alerts using contextual information
Contextual prioritization ranks alerts by likely business impact so engineers address high-value incidents first. Threat scoring evaluates factors like service criticality, customer impact, historical patterns, system load, and dependency mapping to assign priority.
Important attributes include:
- Service criticality: prioritize customer-facing and revenue systems
- Customer impact scope: escalate alerts affecting large user groups
- Historical context: increase priority for services with frequent recent incidents
- Business hours: weigh alerts differently during peak usage
- Dependency mapping: elevate core infrastructure issues above edge services
Prioritized alerts help engineers focus on important issues and systems should also enrich notifications with deployment history, related alerts, affected users, and suggested first steps to speed investigation.
Automate alert triage and response workflows
Automation handles repetitive assessment, enrichment, routing, and escalation so engineers concentrate on resolution. Typical stages are initial assessment, enrichment with logs and metrics, routing to the right team or person, and timed escalation for unacknowledged alerts.
AIOps case studies show an 80% reduction in detection time and MTTR drop from 3 hours to 20 minutes when teams deploy end-to-end automation and decision workflows. Pre-built playbooks codify institutional knowledge, and AI assistants can suggest next actions based on historical incidents and current state.
Automation augments—rather than replaces—human judgment by delivering pre-analyzed, context-rich incidents so engineers spend less time on triage and more on fixing problems.
Use bulk actions to manage alerts efficiently
Bulk actions let teams merge, snooze, dismiss, or escalate many related alerts at once, dramatically reducing manual effort during large incidents or maintenance windows.
Common bulk actions:
- Merge: combine related alerts into one incident thread
- Snooze: suppress expected alerts during maintenance
- Dismiss: remove confirmed false positives
- Escalate: raise severity for multiple related alerts together
| Scenario | Manual actions required | With bulk actions | Time saved |
|---|---|---|---|
| Database outage (50 related alerts) | 50 individual reviews | 1 bulk merge | 95% |
| Planned maintenance (100 alerts) | 100 dismissals | 1 bulk snooze | 99% |
| False positive pattern (25 alerts) | 25 investigations | 1 bulk dismiss | 96% |
Platforms provide auditable, reversible bulk edits so efficiency doesn't sacrifice accountability. Establish clear criteria and guidelines for when to apply bulk actions to avoid masking distinct incidents.
Train and empower your on-call team continuously
Continuous training builds competence, reduces response time, and lowers burnout by preparing engineers for evolving tools and architectures. Combine routine workshops, scenario-based drills, and post-incident debriefs to keep skills and procedures current.
Training elements:
- Hands-on workshops for new tools and updates
- Scenario drills to rehearse high-pressure responses
- Post-incident reviews to capture lessons and improve processes
- Up-to-date documentation and knowledge bases for quick reference
Focus on alert triage best practices, root cause analysis, automation configuration, incident communication, and stress management. Investing in continuous training improves MTTR, decision-making under pressure, and sustainable on-call practices.
Regularly review and optimize alerting strategies
Make alerting improvements continuous: review processes, metrics, and team feedback regularly so alerting stays aligned with system and organizational changes. Quarterly retrospectives focused on alert effectiveness help prevent fatigue from returning.
Key performance indicators:
- Alert-to-incident ratio: alerts that indicate real problems
- False positive rate: percent of non-issues
- Response time metrics: generation-to-acknowledgment times
- Resolution efficiency: speed from alert to fix
- Team satisfaction scores: qualitative workload feedback
A quarterly review framework:
- Metrics analysis: volume, accuracy, and response trends
- Team feedback: frontline experiences and suggestions
- Tool evaluation: platform fit for current needs
- Rule optimization: thresholds, correlation, and routing updates
- Process refinement: workflow and playbook adjustments
Balance quantitative metrics with engineers' subjective experience to ensure optimizations address real operational pain points.
Best practices for on-call scheduling to minimize fatigue
Good scheduling integrates alerting, rotas, and status pages to distribute workload and protect engineers’ recovery time. Follow fairness, limit consecutive shifts, maintain clear handoffs, and plan escalation paths.
Scheduling best practices:
- Rotation fairness: equitable duties considering preferences and expertise
- Consecutive shift limits: avoid back-to-back nights and long stretches
- Clear handoffs: document status, issues, and recent changes at transition
- Escalation planning: defined paths for complex incidents
Rotation strategies:
| Rotation type | Advantages | Best for |
|---|---|---|
| Follow-the-sun | 24/7 local-hours coverage | Global teams |
| Week-on/week-off | Predictable, focused weeks | Teams favoring longer rotations |
| Tiered escalation | Expertise matching, distributed load | Complex systems |
| Shared primary/secondary | Redundancy and knowledge sharing | Small teams |
Modern platforms like incident.io automate schedules, notifications, and coverage requests to keep visibility clear and reduce administrative friction. The aim is sustainable response capability while preserving work-life balance.
Leveraging AI and automation to support on-call engineers
AIOps applies AI and ML to automate operations tasks and elevate alert management beyond static rules. ML summaries and AI-guided workflows give context, suggest actions, and speed diagnosis by correlating historical and current data across systems (example use case).
AIOps impacts include dramatic detection and resolution improvements: case studies show up to an 80% reduction in detection time and MTTR drops from hours to minutes when AI is fed high-quality, centralized data. AI SREs can:
- Suggest investigation steps based on similar incidents
- Auto-gather logs, metrics, and related context
- Predict escalation likelihood and recommend resource allocation
- Route incidents to the best responders and generate post-incident summaries
Success depends on training AI on your organization’s incident history; generic models are less effective than systems tuned to your topology and workflows.
Frequently asked questions about preventing alert fatigue
What causes alert fatigue in modern on-call teams?
Alert fatigue stems from too many, duplicate, or irrelevant notifications across multiple monitoring tools, which desensitizes engineers and makes it hard to spot real emergencies.
How can automation help reduce alert fatigue?
Automation correlates alerts, filters noise, enriches context, and routes incidents to the right people, removing manual triage and ensuring critical issues get immediate attention.
What strategies improve alert prioritization and context?
Use business-impact attributes—service criticality, customer scope, historical incidents, load, and dependency mapping—to score and surface high-priority alerts, and enrich notifications with relevant context and remediation steps.
How does alert fatigue affect team productivity and morale?
Persistent alert fatigue increases burnout, slows resolution, reduces time for proactive work, and lowers morale, leading to higher turnover and degraded operational effectiveness.
What training helps teams manage alerts more effectively?
Combine scenario-based drills, hands-on workshops, up-to-date documentation, and post-incident debriefs so engineers gain practical triage skills, institutional knowledge, and confidence handling incidents.

See related articles

Everything you need to know about ITIL 5, AI and incident management
We break down ITIL 5's governance framework and what it means for teams using AI in incident response. For incident management, it addresses questions like: Who's accountable when an AI-suggested remediation backfires? How do you audit AI-generated updates?
 Chris Evans
Chris Evans
DevEx matters for coding agents, too
When AI can scaffold out entire features in seconds and you have multiple agents all working in parallel on different tasks, a ninety-second feedback loop kills your flow state completely. We've recently invested in dramatically speeding up our developer feedback cycles, cutting some by 95% to address this. In this post we’ll share what that journey looked like, why we did it and what it taught us about building for the AI era.
 Rory Bain
Rory Bain
Stop choosing between fast incident response and secure access
incident.io’s new integration with Opal Security delivers automatic, time-bound production access for on-call engineers, eliminating slow approvals and permanent permissions.
 Brian Hanson
Brian HansonSo good, you’ll break things on purpose
Ready for modern incident management? Book a call with one of our experts today.
We’d love to talk to you about
- All-in-one incident management
- Our unmatched speed of deployment
- Why we’re loved by users and easily adopted
- How we work for the whole organization



